
Share 6 useful suggestions to help confused Cissp candidates get rid of the shackles! And finally successfully passed the ISC CISSP certification exam.
Cissp certification has been around for many years! Candidates will benefit for a long time as long as they can pass the exam!
However, ISC CISSP contains rich certification content, and the certification is relatively difficult. It is not easy to pass the exam successfully!
Before I share my 6 pieces of advice, let me tell you a core answer: Any certification exam requires hard study and practice to ensure a 99% success rate!
Use leads4pass Cissp dumps within a week before the exam: https://www.leads4pass.com/cissp.html (1703 Q&A) to help you simulate the exam to achieve twice the result with half the effort! you can
Use PDF or the VCE Simulation Engine, both formats contain up-to-date exam questions and answers!
Check out 6 Tips:
Understand the CISSP Exam Domains: Familiarize yourself with the eight domains covered in the CISSP Common Body of Knowledge (CBK). These domains include Security and Risk Management, Asset Security, Security Architecture and Engineering, Communication and Network Security, Identity and Access Management (IAM), Security Assessment and Testing, Security Operations, and Software Development Security. Understanding the content and weightage of each domain will guide your study plan.
–>Tip 1
Create a Study Plan: Developing a structured study plan is crucial for efficient preparation. Break down your study material according to the domains and allocate dedicated time for each topic. It’s essential to set realistic goals and establish a consistent study routine to cover all the necessary content before the exam.
–>Tip 2
Leverage Official Study Resources: Utilize the official study resources provided by (ISC)², the organization that administers the CISSP certification. These resources include the Official (ISC)² Guide to the CISSP CBK and the CISSP Study Guide, among others. They are reliable sources and align closely with the exam content.
–>Tip 3
Utilize Supplementary Materials: In addition to official resources, consider using supplementary study materials such as practice exams, online forums, video tutorials, and study groups. These resources can provide different perspectives, additional practice questions, and opportunities for knowledge exchange with other candidates.
–>Tip 4
Focus on Concepts and Application: The CISSP exam emphasizes understanding concepts and their practical application rather than rote memorization. Instead of simply memorizing facts, focus on grasping the underlying principles and how they apply in real-world scenarios. This will help you answer questions that require critical thinking and analysis.
–>Tip 5
Test Yourself with Practice Exams: Practice exams are invaluable for assessing your knowledge and identifying areas that require further study. They also help you become familiar with the format and structure of the CISSP exam. Dedicate time to answering practice questions and reviewing the explanations for both correct and incorrect answers. This process will reinforce your understanding and boost your confidence.
–>Tip 6
What’s more! Read some Cissp exam practice questions and answers for free:
| From | Number of exam questions | Exam name | Update time | Last updated |
| leads4pass | 15 | Certified Information Systems Security Professional | Feb,2025 | Cissp Practice test |
Question 1:
What industry-recognized document could be used as a baseline reference that is related to data security and business operations for conducting a security assessment?
A. Service Organization Control (SOC) 1 Type 2
B. Service Organization Control (SOC) 2 Type 1
C. Service Organization Control (SOC) 1 Type 1
D. Service Organization Control (SOC) 2 Type 2
Correct Answer: B
Question 2:
What is the MAIN purpose for writing planned procedures in the design of Business Continuity Plans (BCP)?
A. Establish lines of responsibility.
B. Minimize the risk of failure.
C. Accelerate the recovery process.
D. Eliminate unnecessary decision-making.
Correct Answer: B
Question 3:
Which of the following is an appropriate source for test data?
A. Production data that is secured and maintained only in the production environment.
B. Test data that has no similarities to production datA.
C. Test data that is mirrored and kept up-to-date with production datA.
D. Production data that has been sanitized before loading into a test environment.
Correct Answer: D
Question 4:
A mobile device application that restricts the storage of user information to just that which is needed to accomplish lawful business goals adheres to what privacy principle?
A. Onward transfer
B. Collection Limitation
C. Collector Accountability
D. Individual Participation
Correct Answer: B
Question 5:
Which of the following is the BEST method to validate secure coding techniques against injection and overflow attacks?
A. Scheduled team review of coding style and techniques for vulnerability patterns
B. Using automated programs to test for the latest known vulnerability patterns
C. The regular use of production code routines from similar applications already in use
D. Ensure code editing tools are updated against known vulnerability patterns
Correct Answer: B
Question 6:
Which of the following is held accountable for the risk to organizational systems and data that result from outsourcing Information Technology (IT) systems and services?
A. The acquiring organization
B. The service provider
C. The risk executive (function)
D. The IT manager
Correct Answer: C
Question 7:
The type of authorized interactions a subject can have with an object is
A. control.
B. permission.
C. procedure.
D. protocol.
Correct Answer: B
Question 8:
Which of the following violates identity and access management best practices?
A. User accounts
B. System accounts
C. Generic accounts
D. Privileged accounts
Correct Answer: C
Question 9:
Which of the following are required components for implementing software configuration management systems?
A. Audit control and signoff
B. User training and acceptance
C. Rollback and recovery processes
D. Regression testing and evaluation
Correct Answer: C
Question 10:
Information Security Continuous Monitoring (1SCM) is defined as maintaining ongoing awareness of information security, vulnerabilities, and threats to support organizational risk management decisions. Which of the following is the FIRST step in developing an ISCM strategy and implementing an ISCM program?
A. Define a strategy based on risk tolerance that maintains clear visibility into assets, awareness of vulnerabilities, up-to-date threat information, and mission/business impacts.
B. Conduct a vulnerability assessment to discover current threats against the environment and incorporate them into the program.
C. Respond to findings with technical management, and operational mitigating activities or acceptance, transference/sharing, or avoidance/rejection.
D. Analyze the data collected and report findings, determining the appropriate response. It may be necessary to collect additional information to clarify or supplement existing monitoring data.
Correct Answer: A
Question 11:
Select and Place:
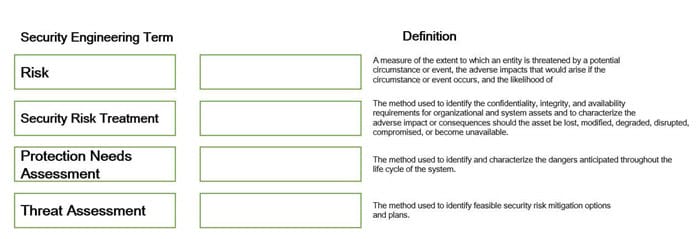
Correct Answer:
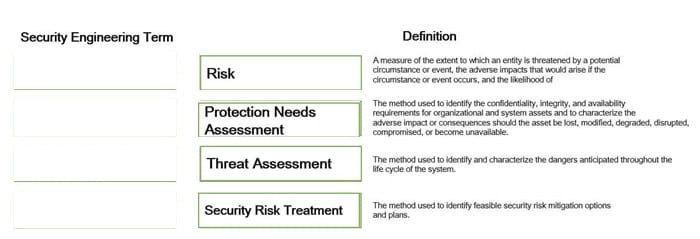
Question 12:
In setting expectations when reviewing the results of a security test, which of the following statements is MOST important to convey to reviewers?
A. The target\’s security posture cannot be further compromised.
B. The results of the tests represent a point-in-time assessment of the target(s).
C. The accuracy of testing results can be greatly improved if the target(s) are properly hardened.
D. The deficiencies identified can be corrected immediately
Correct Answer: C
Question 13:
When resolving ethical conflicts, the information security professional MUST consider many factors. In what order should these considerations be prioritized?
A. Public safety, duties to individuals, duties to the profession, and duties to principals
B. Public safety, duties to principals, duties to individuals, and duties to the profession
C. Public safety, duties to the profession, duties to principals, and duties to individuals
D. Public safety, duties to principals, duties to the profession, and duties to individuals
Correct Answer: B
Question 14:
The 802.1x standard provides a framework for what?
A. Network authentication for only wireless networks
B. Network authentication for wired and wireless networks
C. Wireless encryption using the Advanced Encryption Standard (AES)
D. Wireless network encryption using Secure Sockets Layer (SSL)
Correct Answer: B
Question 15:
What is the MOST important reason to configure unique user IDs?
A. Supporting accountability
B. Reducing authentication errors
C. Preventing password compromise
D. Supporting Single Sign On (SSO)
Correct Answer: A
PS. Download free shareable Cissp exam practice questions and answers: https://drive.google.com/file/d/10MZ0opLu0GBiG66E91yylB4g8_W5GKQ3/view?usp=sharing
Cissp dumps complete learning list:
| Single & multiple choice | 1679 |
| Drog drop | 19 |
| Hospot | 5 |
Download Cissp dumps with PDF and VCE: https://www.leads4pass.com/cissp.html (contains 1703 latest exam questions and answers!)
Remember, CISSP is a comprehensive certification that requires a deep understanding of various security domains. Give yourself ample time to prepare and adopt a consistent and disciplined approach to studying. Good luck with your CISSP certification journey!



![[2021.3] leads4pass cissp practice test q6](https://www.examfast.com/wp-content/uploads/2021/03/q6.jpg)
![[2021.3] leads4pass cissp practice test q6-1](https://www.examfast.com/wp-content/uploads/2021/03/q6-1.jpg)