
Are you ready to take the Isaca Certified Information Systems Auditor CISA exam?
Next, I will share the latest CISA exam dumps, exam practice questions, and exam details! Help you pass the exam successfully!
CISA Exam Dumps:
The latest update of lead4Pass CISA exam dumps comes with two modes: PDF and VCE. You can choose your favorite model or both!
The newly updated exam questions contain 3525 exam questions and answers! Guarantee true and effectiveness.
Visit URL:https://www.leads4pass.com/cisa.html (3525Q&A)
CISA Exam Practice Questions:
You can take part in the CISA exam practice test shared for free on this site to test your strength! All free exam questions are shared by leads4pass. Please participate in the exercise first, and the test answers will be announced at the end of the article. Of course, we also shared the corresponding CISA exam PDF for free, which you can download online for free.
CISA Exam details:
Register online for the CISA certification exam. The exam is available either online with remote proctoring or in person at a testing center. Download the CISA Planning Guide for more information.
Eligibility is established at the time of exam registration and is good for twelve (12) months (365 days).
Exam registration and payment are required before you can schedule and take an exam.
You will forfeit your fees if you do not schedule and take the exam during your 12-month eligibility period.
No eligibility deferrals or extensions are allowed.
The final step to becoming CISA certified is to submit your CISA Certification Application. Prior to doing so, you must meet the following requirements:
Pass the CISA Exam within the last 5 years.
Have the relevant full-time work experience in the CISA exam content outline.
Submit the CISA Certification Application including the application processing fee.
Next, please participate in the CISA exam practice
QUESTION 1
A large chain of shops with electronic funds transfer (EFT) at point-of-sale devices has a central communications processor for connecting to the banking network. Which of the following is the BEST
disaster recovery plan for the communications processor?
A. Offsite storage of daily backups
B. Alternative standby processor onsite
C. installation of duplex communication links
D. Alternative standby processor at another network node
Having an alternative standby processor at another network node would be the best solution. The unavailability of the central communications processor would disrupt all access to the banking network, resulting in the disruption of operations for all of the shops. This could be caused by failure of equipment, power or communications. Offsite storage of backups would not help, since EFT tends to be an online process and offsite storage will not replace the dysfunctional processor. The provision of an alternate processor onsite would be fine if it were an equipment problem, but would not help in the case of a power outage, installation of duplex communication links would be most appropriate if it were only the communication link that failed.
QUESTION 2
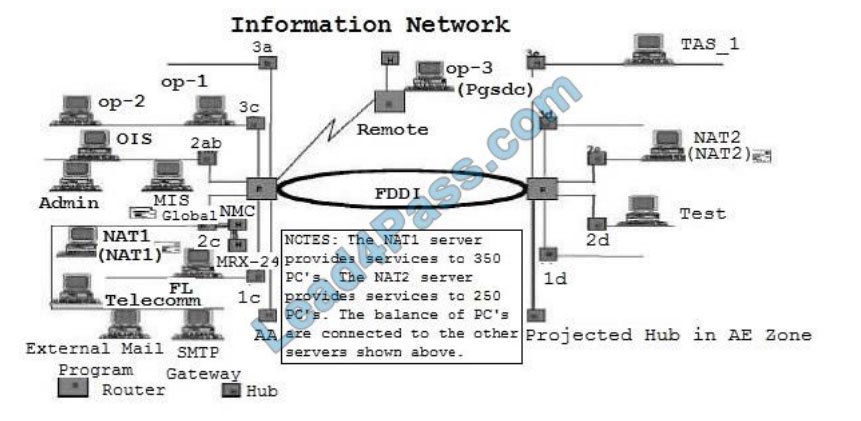
For locations 3a, 1d and 3d, the diagram indicates hubs with lines that appear to be open and active. Assuming that is true, what control, if any, should be recommended to mitigate this weakness?
A. Intelligent hub
B. Physical security over the hubs
C. Physical security and an intelligent hub
D. No controls are necessary since this is not a weakness
Open hubs represent a significant control weakness because of the potential to access a network connection easily. An intelligent hub would allow the deactivation of a single port while leaving the remaining ports active. Additionally, physical security would also provide reasonable protection over hubs with active ports.
QUESTION 3
The risk that the IS auditor will not find an error that has occurred is identified by which of the following terms?
A. Control
B. Prevention
C. Inherent
D. Detection
QUESTION 4
Which of the following controls would BEST decrease the exposure if a password is compromised?
A. Passwords are masked.
B. Passwords are encrypted.
C. Passwords have format restrictions.
D. Password changes are forced periodically.
QUESTION 5
Which testing approach is MOST appropriate to ensure that internal application interface errors are identified as soon as possible?
A. Bottom up
B. Sociability testing
C. Top-down
D. System test
The top-down approach to testing ensures that interface errors are detected early and that testing of major functions is conducted early. A bottom-up approach to testing begins with atomic units, such as programs and modules, and works upward until a complete system test has taken place. Sociability testing and system tests take place at a later stage in the development process.
QUESTION 6
Which of the following BEST enables timely detection of changes in the IT environment to support informed decision making by management?
A. Continuous monitoring
B. Sampling checks on high-risk areas
C. Change management reports
D. Established key risk indicators (KRIs)
QUESTION 7
Security administration procedures require read-only access to:
A. access control tables.
B. security log files.
C. logging options.
D. user profiles.
Security administration procedures require read-only access to security log files to ensure that, once generated, the logs are not modified. Logs provide evidence and track suspicious transactions and activities. Security administration procedures require write access to access control tables to manage and update the privileges according to authorized business requirements. Logging options require write access to allow the administrator to update the way the transactions and user activities are monitored, captured, stored, processed and reported.
QUESTION 8
Which of the following would BEST maintain the integrity of a firewall log?
A. Granting access to log information only to administrators
B. Capturing log events in the operating system layer
C. Writing dual logs onto separate storage media
D. Sending log information to a dedicated third-party log server
Establishing a dedicated third-party log server and logging events in it is the best procedure for maintaining the integrity of a firewall log. When access control to the log server is adequately maintained, the risk of unauthorized log modification will be mitigated, therefore improving the integrity of log information. To enforce segregation of duties, administrators should not have access to log files. This primarily contributes to the assurance of confidentiality rather than integrity. There are many ways to capture log information: through the application layer, network layer, operating systems layer, etc.; however, there is no log integrity advantage in capturing events in the operating systems layer. If it is a highly mission-critical information system, it may be nice to run the system with a dual log mode. Having logs in two different storage devices will primarily contribute to the assurance of the availability of log information, rather than to maintaining its integrity.
QUESTION 9
Which of the following is the MOST effective method for dealing with the spreading of a network worm that exploits vulnerability in a protocol?
A. Install the vendor\\’s security fix for the vulnerability.
B. Block the protocol traffic in the perimeter firewall.
C. Block the protocol traffic between internal network segments.
D. Stop the service until an appropriate security fix is installed.
Stopping the service and installing the security fix is the safest way to prevent the worm from spreading, if the service is not stopped, installing the fix is not the most effective method because the worm continues spreading until the fix
becomes effective. Blocking the protocol on the perimeter does not stop the worm from spreading to the internal
network(s). Blocking the protocol helps to slow down the spreading but also prohibits any software that utilizes it from
working between segments.
QUESTION 10
A new information security manager is charged with reviewing and revising the information security strategy. The information security manager\\’s FIRST course of action should be to gain an understanding of the organization\\’s:
A. security architecture
B. risk register
C. internal control framework
D. business strategy
QUESTION 11
Which of the following is the GREATEST risk of an inadequate policy definition for ownership of data and systems?
A. User management coordination does not exist.
B. Specific user accountability cannot be established.
C. Unauthorized users may have access to originate, modify or delete data.
D. Audit recommendations may not be implemented.
Without a policy defining who has the responsibility for granting access to specific systems, there is an increased risk that one could gain (be given) system access when they should not have authorization. By assigning authority to grant access to specific users, there is a better chance that business objectives will be properly supported.
QUESTION 12
Following a malicious security incident, an organization has decided to prosecute those responsible. Which of the following will BEST facilitate the forensic investigation?
A. Identifying the affected environment
B. Performing a backup of affected systems
C. Determining the degree of loss
D. Maintaining chain of custody
QUESTION 13
A. Adequate resourcing for the incident response team
B. Adequate encryption between applications
C. Adequate application clustering
D. Adequate reciprocal recovery agreement
Publish the answer:
| Q1` | Q2 | Q3 | Q4 | Q5 | Q6 | Q7 | Q8 | Q9 | Q10 | Q11 | Q12 | Q13 |
| D | C | D | D | C | A | B | D | D | D | C | D | C |
Isaca CISA exam PDF free sharing
Google Drive: https://drive.google.com/file/d/1UdToCAdAomLRsOi8wqU4PrJCQey50EN5/view?usp=sharing
Thanks for reading, this site has shared the leads4pass CISA dumps https://www.leads4pass.com/cisa.html, exam practice test, exam details, exam core. I wish you success in passing the exam!
If you like, please bookmark and share!

