
leads4pass 200-201 dumps with PDF and VCE contains the latest 264 exam questions and answers, the best exam material for the 2022-2023 200-201 CBROPS certification exam.
Candidates use 2022-2023 200-201 dumps https://www.leads4pass.com/200-201.html, to help them practice the target task exam questions and answers, and ultimately successfully pass the 200-201 CBROPS certification exam.

Read some free leads4pass 200-201 dumps exam questions and answers online
| Number of exam questions | Exam name | Exam code |
| 15 | Threat Hunting and Defending using Cisco Technologies for CyberOps (CBROPS) | 200-201 |
Question 1:
What is a collection of compromised machines that attackers use to carry out a DDoS attack?
A. subnet
B. botnet
C. VLAN
D. command and control
Correct Answer: B
Question 2:
Refer to the exhibit.
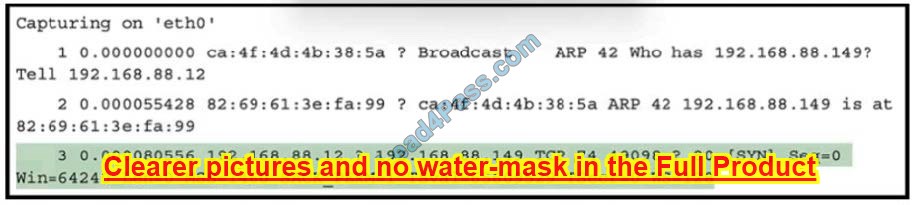
What must be interpreted from this packet capture?
A. IP address 192.168.88 12 is communicating with 192 168 88 149 with a source port 74 to destination port 49098 using TCP protocol
B. IP address 192.168.88.12 is communicating with 192 168 88 149 with a source port 49098 to destination port 80 using TCP protocol.
C. IP address 192.168.88.149 is communicating with 192.168 88.12 with a source port 80 to destination port 49098 using TCP protocol.
D. IP address 192.168.88.149 is communicating with 192.168.88.12 with a source port 49098 to destination port 80 using TCP protocol.
Correct Answer: B
Question 3:
Which technology on a host is used to isolate a running application from other applications?
A. sandbox
B. application allows a list
C. application block list
D. host-based firewall
Correct Answer: A
Question 4:
An investigator is examining a copy of an ISO file that is stored in PDF format. What type of evidence is this file?
A. data from a CD copied using a Mac-based system
B. data from a CD copied using a Linux system
C. data from a DVD copied using the Windows system
D. data from a CD copied using Windows
Correct Answer: B
CDFs is a virtual file system for Unix-like operating systems; it provides access to data and audio tracks on Compact Discs. When the CDfs driver mounts a Compact Disc, it represents each track as a file. This is consistent with the Unix convention “everything is a file”.
Source: https://en.wikipedia.org/wiki/CDfs
Question 5:
What is the difference between tampered and untampered disk images?
A. Tampered images have the same stored and computed hash.
B. Tampered images are used as evidence.
C. Untampered images are used for forensic investigations.
D. Untampered images are deliberately altered to preserve evidence
Correct Answer: B
Question 6:
What is threat hunting?
A. Managing a vulnerability assessment report to mitigate potential threats.
B. Focusing on proactively detecting possible signs of intrusion and compromise.
C. Pursuing competitors and adversaries to infiltrate their system to acquire intelligence data.
D. Attempting to deliberately disrupt servers by altering their availability
Correct Answer: B
Question 7:
Which evasion technique is indicated when an intrusion detection system begins receiving an abnormally high volume of scanning from numerous sources?
A. resource exhaustion
B. tunneling
C. traffic fragmentation
D. timing attack
Correct Answer: A
Resource exhaustion is a type of denial-of-service attack; however, it can also be used to evade detection by security defenses. A simple definition of resource exhaustion is “consuming the resources necessary to perform an action.”
Question 8:
What is the impact of false positive alerts on business compared to true positives?
A. True positives affect security as no alarm is raised when an attack has taken place, while false positives are alerts raised appropriately to detect and further mitigate them.
B. True-positive alerts are blocked by mistake as potential attacks, while False-positives are actual attacks Identified as harmless.
C. False-positive alerts are detected by confusion as potential attacks, while true positives are attack attempts identified appropriately.
D. False positive alerts are manually ignored signatures to avoid warnings that are already acknowledged, while true positives are warnings that are not yet acknowledged.
Correct Answer: C
Question 9:
What is the benefit of using asymmetric cryptography?
A. decrypts data with one key
B. fast data transfer
C. secure data transfer
D. encrypts data with one key
Correct Answer: B
Question 10:
What is the relationship between a vulnerability and a threat?
A. A threat exploits a vulnerability
B. A vulnerability is a calculation of the potential loss caused by a threat
C. A vulnerability exploits a threat
D. A threat is a calculation of the potential loss caused by a vulnerability
Correct Answer: A
Question 11:
What is the difference between inline traffic interrogation and traffic mirroring?
A. Inline interrogation is less complex as traffic mirroring applies additional tags to data.
B. Traffic mirroring copies the traffic rather than forwarding it directly to the analysis tools
C. Inline replicates the traffic to preserve integrity rather than modifying packets before sending them to other analysis tools.
D. Traffic mirroring results in faster traffic analysis and inline is considerably slower due to latency.
Correct Answer: A
Question 12:
Which data type is necessary to get information about source/destination ports?
A. statistical data
B. session data
C. connectivity data
D. alert data
Correct Answer: B
Session data provides information about the five tuples; source IP address/port number, destination IP address/port number, and the protocol What is Connectivity Data? According to IBM – Connectivity data defines how entities are connected in the network. It includes connections between different devices, and VLAN- related connections within the same device https://www.ibm.com/docs/en/networkmanager/4.2.0?topic=relationships-connectivity-data
Question 13:
During which phase of the forensic process is data that is related to a specific event labeled and recorded to preserve its integrity?
A. examination
B. investigation
C. collection
D. Reporting
Correct Answer: C
Question 14:
Which HTTP header field is used in forensics to identify the type of browser used?
A. referrer
B. host
C. user-agent
D. accept-language
Correct Answer: C
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:12.0) Gecko/20100101 Firefox/12.0 In computing, a user agent is any software, acting on behalf of a user, which “retrieves, renders and facilitates end-user interaction with Web content”.[1] A user agent is therefore a special kind of software agent. https://en.wikipedia.org/wiki/User_agent#User_agent_identification A user agent is a computer program representing a person, for example, a browser in a Web context. https://developer.mozilla.org/en-US/docs/Glossary/User_agent
Question 15:
What is the difference between inline and tap mode traffic monitoring?
A. Inline monitors traffic without examining other devices, while a tap mode tags traffic and examines the data from monitoring devices.
B. Tap mode monitors traffic direction, while inline mode keeps packet data as it passes through the monitoring devices.
C. Tap mode monitors packets and their content with the highest speed, while the inline mode draws a packet path for analysis.
D. Inline mode monitors traffic path, examining any traffic at a wire speed, while tap mode monitors traffic as it crosses the network.
Correct Answer: D
…
Candidates use 2022-2023 200-201 dumps https://www.leads4pass.com/200-201.html, to help them practice the target task exam questions and answers, and ultimately successfully pass the 200-201 CBROPS certification exam.
