Get your Cisco ICND1 100-105 dumps exam preparation questions in form of 100-105 PDF. leads4pass is the best site for providing online preparation material for 100-105 exam. “Cisco Interconnecting Cisco Networking Devices Part 1 (ICND1 v3.0)” is the name of Cisco ICND1 https://www.leads4pass.com/100-105.html exam dumps which covers all the knowledge points of the real Cisco exam. Cisco ICND1 100-105 dumps exam preparation kit contains all the necessary 100-105 questions that you need to know.
Vendor: Cisco
Certifications: ICND1100-105
Exam Name: Cisco Interconnecting Cisco Networking Devices Part 1 (ICND1 v3.0)
Exam Code: 100-105
Total Questions: 347 Q&As
Best Cisco 100-105 dumps pdf training resources: https://drive.google.com/open?id=0B_7qiYkH83VReEJYRlhNVjdGeVU
Best Cisco 200-105 dumps pdf training resources: https://drive.google.com/open?id=0B_7qiYkH83VRS3BsT2duT3pTSlU
With the help of latest and authentic Cisco ICND1 100-105 dumps exam questions, you can find the best 100-105 ICND1 – Cisco exam preparation kit here and you will also get the 100% guarantee for passing the Cisco exam. Latest Cisco 100-105 dumps real exam questions and answers (1-12) update demo. Download the best useful Cisco ICND1 100-105 dumps vce software free try.
2018 New Cisco ICND1 100-105 Dumps Exam Questions And Answers (13-30)
QUESTION 13
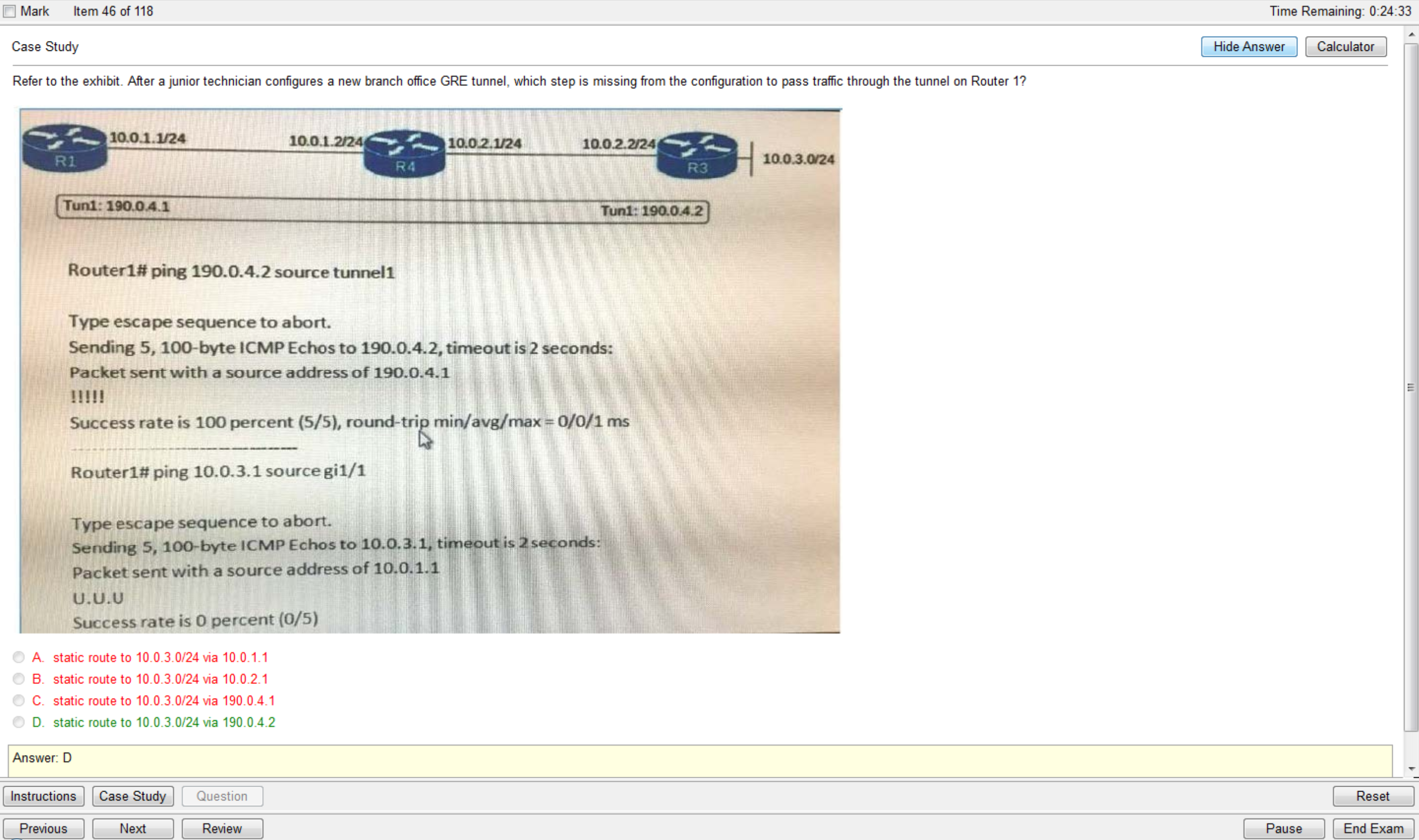
Refer to the exhibit.
A network technician is unable to ping from R1 to R2. What will help correct the problem?
A. Ensure that the serial cable is correctly plugged in to the interfaces.
B. Apply the clock rate 56000 configuration command to the serial0/1 interface of R1.
C. Configure the serial0/1 interfaces on R1 and R2 with the no shutdown command.
D. Change the address of the serial0/1 interface of R1 to 192.1.1.4.
E. Change the subnet masks of both interfaces to 255.255.255.240.
Correct Answer: A
QUESTION 14
Which command can you enter to verify that a 128-bit address is live and responding?
A. traceroute
B. telnet
C. ping
D. ping ipv6
Correct Answer: C
QUESTION 15
Which port-security feature allows a switch to learn MAC addresses dynamically and add them to the running configuration?
A. security violation restrict mode
B. switch port protection
C. sticky learning
D. security violation protect mode
Correct Answer: C
Explanation:
You can configure an interface to convert the dynamic MAC addresses tosticky secure MAC addresses and to add them to the running configuration by enabling sticky learning. To enable sticky learning, enter the switchport port-security macaddress sticky interface configuration command. When you enter this command, the interface converts all the dynamic secure MAC addresses, including those that were dynamically learned before sticky learning was enabled, to sticky secure MAC addresses.
QUESTION 16
Which transport layer protocol is best suited for the transport of VoIP data?
A. RIP
B. UDP
C. TCP
D. OSPF
E. HTTP
Correct Answer: B
QUESTION 17
CORRECT TEXT
How do you bypass password on cisco device?
A. Change the configuration register to 0x2142. With this setting when that router reboots, it bypasses the startup-config and no password is required.
Correct Answer: A
QUESTION 18
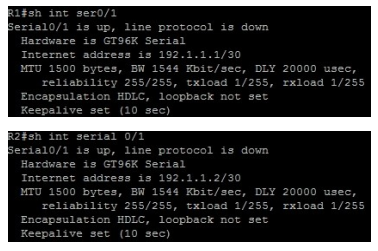
Refer to the exhibit.
What value should be displayed in Box 1 of the ipconfig output of host A?
A. 172.18.14.5
B. 172.18.14.6
C. 192.168.1.10
D. 192.168.1.11
E. 192.168.1.250
F. 192.168.1.254
Correct Answer: F
QUESTION 19
In which two ways does TCP differ from UDP? (Choose two.)
A. TCP segments are essentially datagrams.
B. TCP uses broadcast delivery.
C. TCP provides sequence numbering of packets.
D. TCP provides synchronized communication.
E. TCP provides best effort delivery
Correct Answer: CD
Explanation:
Before two computers can communicate over TCP, they must synchronize their initial sequence numbers (ISN) TCP uses a sequence number to identify each byte of data. The sequence number identifies the order of the bytes sent from each computer so that the data can be reconstructed in order, regardless of any fragmentation, disordering, or packet loss that may occur during
QUESTION 20
What is true about ipv6 unique local addresses:
A. Global id
B. Public routable
C. Summarization
D. Unique prefix
Correct Answer: D
QUESTION 21
Which feature allows a device to use a switch port that is configured for half-duplex to access the network?
A. CSMA/CD
B. IGMP
C. port security
D. split horizon
Correct Answer: A
Explanation:
Ethernet began as a local area network technology that provided a half-duplex shared channel for stations connected to coaxial cable segments linked with signal repeaters. In this appendix, we take a detailed look at the half-duplex sharedchannel mode of operation, and at the CSMA/CD mechanism that makes it work.
In the original half-duplex mode, the CSMA/CD protocol allows a set of stations to compete for access to a shared Ethernet channel in a fair and equitable manner. The protocol’s rules determine the behavior of Ethernet stations, including when they are allowed to transmit a frame onto a shared Ethernet channel, and what to do when a collision occurs. Today, virtually all devices are connected to Ethernet switch ports over full-duplex media, such as twisted-pair cables. On this type of connection, assuming that both devices can support the full-duplex mode of operation and that Auto-Negotiation (AN) is enabled, the AN protocol will automatically select the highest-performance mode of operation supported by the devices at each end of the link. That will result in full-duplex mode for the vast majority of Ethernet connections with modern interfaces that support full duplex and AN.
QUESTION 22
Which statement about the inside interface configuration in a NAT deployment is true?
A. It is defined globally
B. It identifies the location of source addresses for outgoing packets to be translated using access or route maps.
C. It must be configured if static NAT is used
D. It identifies the public IP address that traffic will use to reach the internet.
Correct Answer: B
Explanation:
This module describes how to configure Network Address Translation (NAT) for IP address conservation and how to configure inside and outside source addresses. This module also provides information about the benefits of configuring NAT for IP address conservation. NAT enables private IP internetworks that use nonregistered IP addresses to connect to the Internet. NAT operates on a device, usually connecting two networks, and translates the private (not globally unique) addresses in the internal network into legal addresses before packets are forwarded onto another network. NAT can be configured to advertise to the outside world only one address for the entire network. This ability provides additional security by effectively hiding the entire internal network behind that one address. NAT is also used at the enterprise edge to allow internal users access to the Internet and to allow Internet access to internal devices such as mail servers.
QUESTION 23
Which value is indicated by the next hop in a routing table?
A. preference of the route source
B. IP address of the remote router for forwarding the packets
C. how the route was learned
D. exit interface IP address for forwarding the packets
Correct Answer: D
Explanation:
The routing table contains network/next hop associations. These associations tell a router that a particular destination can be optimally reached by sending the packet to a specific router that represents the “next hop” on the way to the final destination. The next hop association can also be the outgoing or exit interface to the final destination.
QUESTION 24
Which route source code represents the routing protocol with a default administrative distance of 90 in the routing table?
A. S
B. E
C. D
D. R
E. O
Correct Answer: C
Explanation:
SStatic
EEGP
DEIGRP
RRIP
OOSPF
Default Administrative distance of EIGRP protocol is 90 then answer is C
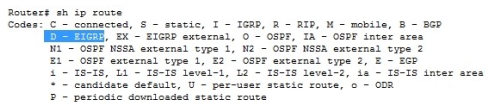
Default Distance Value TableThis table lists the administrative distance default values of the protocols that Cisco supports:
Route Source
Default Distance Values
Connected interface
Static route
Enhanced Interior Gateway Routing Protocol (EIGRP) summary route External Border Gateway Protocol (BGP)
Internal EIGRP
IGRP
OSPF
Intermediate System-to-Intermediate System (IS-IS) Routing Information Protocol (RIP)
Exterior Gateway Protocol (EGP)
On Demand Routing (ODR)
External EIGRP
Internal BGP
Unknown*
QUESTION 25
![]()
Refer to the exhibit. Which feature is enabled by this configuration?
A. static NAT translation
B. a DHCP pool
C. a dynamic NAT address pool
D. PAT
Correct Answer: C
QUESTION 26
Which statement about a router on a stick is true?
A. Its date plane router traffic for a single VI AN over two or more switches.
B. It uses multiple subinterfaces of a single interface to encapsulate traffic for different VLANs on the same subnet.
C. It requires the native VLAN to be disabled.
D. It uses multiple subinterfaces of a single interface to encapsulate traffic for different VLANs.
Correct Answer: D
QUESTION 27
Refer to the exhibit. The network administrator must complete the connection between the RTA of the XYZ Company and the service provider. To accomplish this task, which two devices could be installed at the customer site to provide a connection through the local loop to the central office of the provider? (Choose two.)
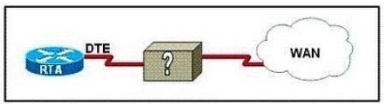
A. WAN switch
B. PVC
C. ATM switch
D. multiplexer
E. CSU/DSU
F. modem
Correct Answer: EF
QUESTION 28
Which adverse situation can occur if an Ethernet cable is too long?
A. late collisions
B. giants
C. interface resets
D. runts
Correct Answer: A
QUESTION 29
Refer to the exhibit.
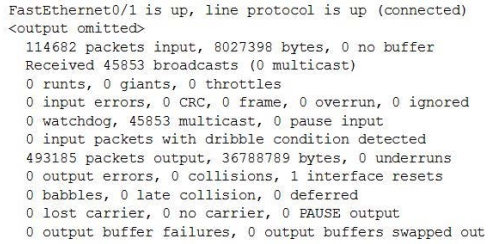
Which two of the output fields could help you determine if a broadcast storm has occurred? (Choose two.)
A. giants
B. no buffer
C. collisions
D. ignored
E. dribble condition
Correct Answer: BD
QUESTION 30
Configuration of which option is required on a Cisco switch for the Cisco IP phone to work?
A. PortFast on the interface
B. the interface as an access port to allow the voice VLAN ID
C. a voice VLAN ID in interface and global configuration mode
D. Cisco Discovery Protocol in global configuration mode
Correct Answer: B
Explanation:
When you connect an IP phone to a switch using a trunk link, it can cause high CPU utilization in the switches. As all the VLANs for a particular interface are trunked to the phone, it increases the number of STP instances the switch has to manage. This increases the CPU utilization. Trunking also causes unnecessary broadcast / multicast / unknown unicast traffic to hit the phone link.
In order to avoid this, remove the trunk configuration and keep the voice and access VLAN configured along with Quality of Service (QoS). Technically, it is still a trunk, but it is called a Multi-VLAN Access Port (MVAP). Because voice and data traffic can travel through the same port, you should specify a different VLAN for each type of traffic. You can configure a switch port to forward voice and data traffic on different VLANs. Configure IP phone ports with a voice VLAN configuration. This configuration creates a pseudo trunk, but does not require you to manually prune the unnecessary VLANs. The voice VLAN feature enables access ports to carry IP voice traffic from an IP phone. You can configure a voice VLAN with the “switchport voice vlan …” command under interface mode. The full configuration is shown below:
Switch(config)#interface fastethernet0/1
Switch(config-if)#switchport mode access
Switch(config-if)#switchport access vlan 10
Switch(config-if)#switchport voice vlan 20
Configure the Switch Port to Carry Both Voice and Data TrafficWhen you connect an IP phone to a switch using a trunk link, it can cause high CPU utilization in the switches. As all the VLANs for a particular interface are trunked to the phone, it increases the number of STP instances the switch has to manage. This increases the CPU utilization. Trunking also causes unnecessary broadcast / multicast / unknown unicast traffic to hit the phone link.
In order to avoid this, remove the trunk configuration and keep the voice and access VLAN configured along with Quality of Service (QoS). Technically, it is still a trunk, but it is called a Multi-VLAN Access Port (MVAP). Because voice and data traffic can travel through the same port, you should specify a different VLAN for each type of traffic. You can configure a switch port to forward voice and data traffic on different VLANs. Configure IP phone ports with a voice VLAN configuration. This configuration creates a pseudo trunk, but does not require you to manually prune the unnecessary VLANs.
The voice VLAN feature enables access ports to carry IP voice traffic from an IP phone. The voice VLAN feature is disabled by default. The Port Fast feature is automatically enabled when voice VLAN is configured. When you disable voice VLAN, the Port Fast feature is not automatically disabled.
Download Cisco ICND1 real 100-105 exam questions and verified answers. 100% passing guarantee and full refund in case of failure https://www.leads4pass.com/100-105.html. If you are looking to get Cisco Interconnecting Cisco Networking Devices Part 1 (ICND1 v3.0) certification by passing exam 100-105 then you can pass it in one go.
Latest Cisco ICND1 100-105 dumps vce youtube: https://youtu.be/wuQgBRPR4rg
